In this article, I will explain how to create a new Azure Active Directory (Azure AD) application and service principal that can be used with the role-based access control. The service principal can be used with PowerShell or to discover Azure resources via Azure API for instance.
Open Azure AD

Go to App Registrations
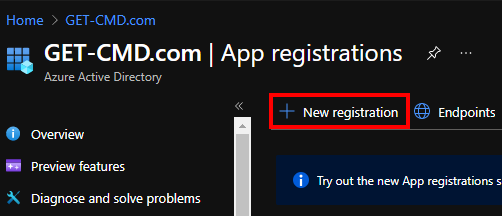
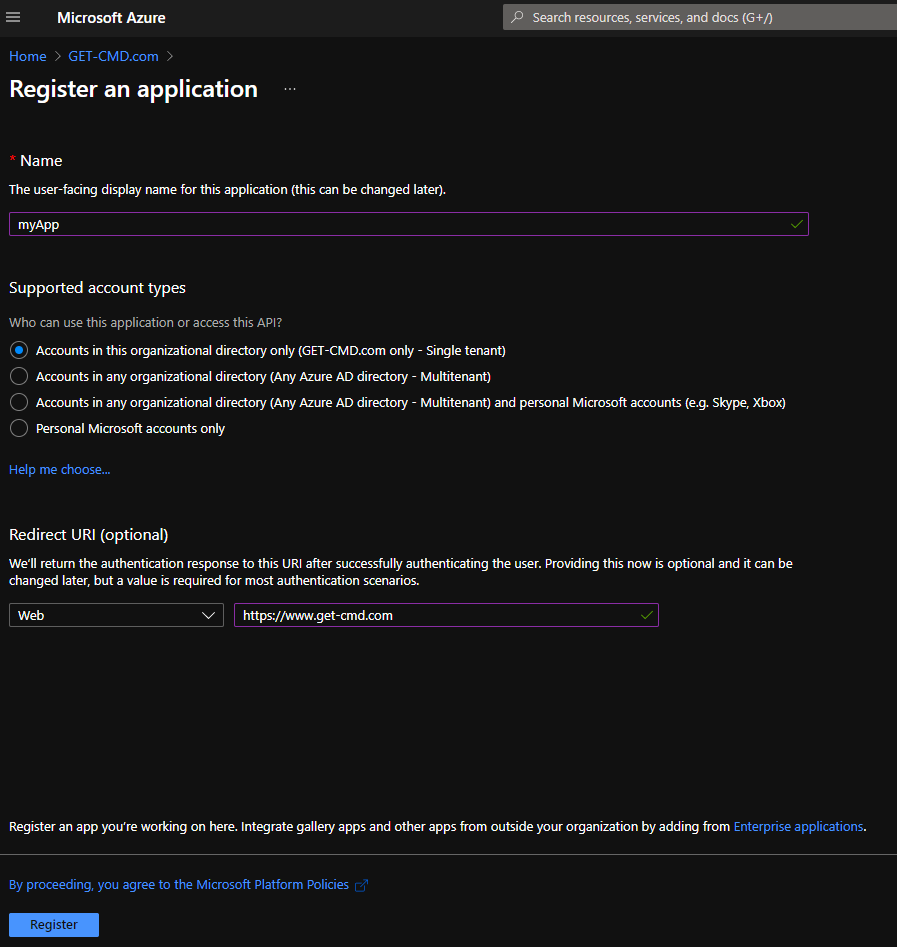
Enter a friendly name for your App and select the account type:
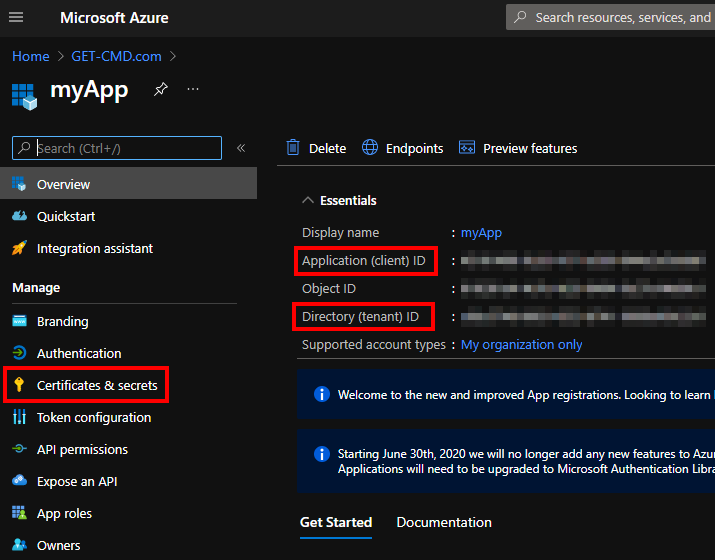
You must copy the App ID which is also known as the “client ID” and the Directory ID which is also known as the “tenant ID”. Then, go to “certificates & secrets”
Click “New client secret” to create the secret
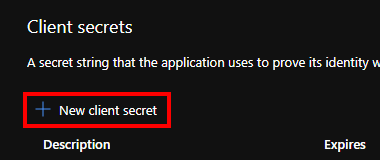
Depending on your needs, you must select the expiration
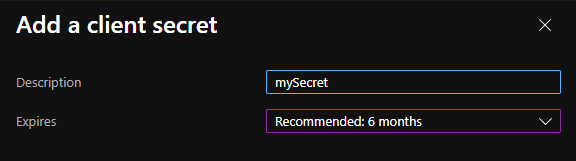
Do not forget to copy the secret, then go to subsscription

In the IAM section, add the Azure App previously created
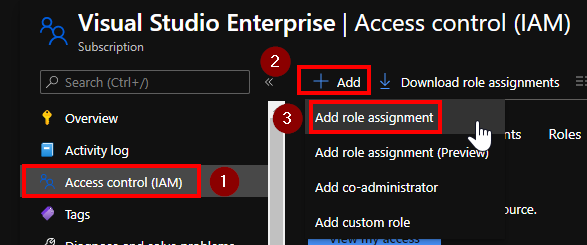
You can adjust the role that you want
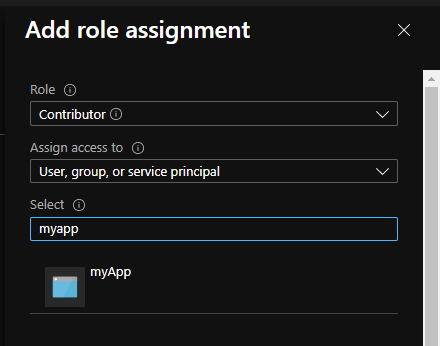
Click “OK” to validate. Then you can for instance use the App with the following PowerShell code:
<code>Connect-AzAccount -ServicePrincipal</code>
By adding the “ServicePrincipal” argument, PowerShell will understand that you try to connect with the Azure App
- Login = Client ID (or Application ID)
- Password = Secret
Thanks for reading! You can follow me on Twitter @PrigentNico

