Azure Active Directory PowerShell for Graph is a PowerShell module used to manage Azure Active Directory. Thanks to this module you can:
- Retrieve data from the directory,
- Create new objects,
- Update existing objects,
- Remove objects,
- and configure the directory.
The Azure AD PowerShell for Graph module has two versions:
- a Public preview version
- a General Availability version. (https://www.powershellgallery.com/packages/AzureAD)
It’s not recommended to use the Public Preview version for production scenarios but you use it to test the PowerShell module.
Let’s see how to install the Preview Module. Open a PowerShell console as administrator:
PS C:\WINDOWS\system32> Install-Module -Name AzureADPreview Untrusted repository You are installing the modules from an untrusted repository. If you trust this repository, change its InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from 'PSGallery'? [Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): Y PS C:\WINDOWS\system32>
If you want to install the Public Module:
PS > Install-Module AzureAD
You must first connect the Connect-AzureAD cmdlet to connect to your Azure Active Directory:
PS C:\WINDOWS\system32> Connect-AzureAD -TenantId xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx Account Environment TenantId TenantDomain AccountType ------- ----------- -------- ------------ ----------- yyyyyyyyyy@yyyyyy.yyy AzureCloud xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx yourdomain.onmicrosoft.com User
Use the Get-Command cmdlet to retrieve all the AzureAD cmdlets:
PS C:\WINDOWS\system32> get-command -Module *AzureAD* CommandType Name Version Source ----------- ---- ------- ------ Cmdlet Add-AzureADAdministrativeUnitMember 2.0.1.2 AzureADPreview Cmdlet Add-AzureADApplicationOwner 2.0.1.2 AzureADPreview Cmdlet Add-AzureADApplicationPolicy 2.0.1.2 AzureADPreview Cmdlet Add-AzureADDeviceRegisteredOwner 2.0.1.2 AzureADPreview Cmdlet Add-AzureADDeviceRegisteredUser 2.0.1.2 AzureADPreview Cmdlet Add-AzureADDirectoryRoleMember 2.0.1.2 AzureADPreview Cmdlet Add-AzureADGroupMember 2.0.1.2 AzureADPreview Cmdlet Add-AzureADGroupOwner 2.0.1.2 AzureADPreview [...]
Now I can easily retrieve information about my Azure AD Domain:
PS C:\WINDOWS\system32> Get-AzureADDomain | fl *
AuthenticationType : Managed
AvailabilityStatus :
ForceDeleteState :
IsAdminManaged : True
IsDefault : True
IsInitial : True
IsRoot : True
IsVerified : True
Name : yourdomain.onmicrosoft.com
State :
SupportedServices : {Email, OfficeCommunicationsOnline}
I can create a new Azure AD User account using the following command:
PS C:\WINDOWS\system32> $PasswordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile PS C:\WINDOWS\system32> $PasswordProfile.Password = "YOUR_PWD" PS C:\WINDOWS\system32> New-AzureADUser -AccountEnabled $True -DisplayName "Nico Prigent" -PasswordProfile $PasswordProfile -Ma ilNickName "NicoP" -UserPrincipalName "Nico@yourdomain.onmicrosoft.com" ObjectId DisplayName UserPrincipalName UserType -------- ----------- ----------------- -------- xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx Nico Prigent Nico@yourdomain.onmicrosoft.com Member
Let’s check if the user exists:
PS C:\WINDOWS\system32> Get-AzureADUser | ? {$_.DisplayName -eq "Nico Prigent"} | fl *
ExtensionProperty : {[odata.type, Microsoft.DirectoryServices.User], [ageGroup, ], [consentProvidedForMinor, ],
[employeeId, ]...}
DeletionTimestamp :
ObjectId : xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
ObjectType : User
AccountEnabled : True
AssignedLicenses : {}
AssignedPlans : {}
City :
CompanyName :
Country :
CreationType :
Department :
DirSyncEnabled :
DisplayName : Nico Prigent
FacsimileTelephoneNumber :
GivenName :
IsCompromised :
ImmutableId :
JobTitle :
LastDirSyncTime :
Mail :
MailNickName : NicoP
Mobile :
OnPremisesSecurityIdentifier :
OtherMails : {}
PasswordPolicies :
PasswordProfile : class PasswordProfile {
Password:
ForceChangePasswordNextLogin: True
EnforceChangePasswordPolicy: False
}
PhysicalDeliveryOfficeName :
PostalCode :
PreferredLanguage :
ProvisionedPlans : {}
ProvisioningErrors : {}
ProxyAddresses : {}
RefreshTokensValidFromDateTime : 03/24/2018 11:07:29
ShowInAddressList :
SignInNames : {}
SipProxyAddress :
State :
StreetAddress :
Surname :
TelephoneNumber :
UsageLocation :
UserPrincipalName : Nico@yourdomain.onmicrosoft.com
UserType : Member
Great, the user exists, so I can now update information using the following commands:
# Retrieve user information
PS C:\WINDOWS\system32> $user = Get-AzureADUser -ObjectId xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
# Let's check the content of the variable
PS C:\WINDOWS\system32> $user
ObjectId DisplayName UserPrincipalName UserType
-------- ----------- ----------------- --------
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx Nico Prigent Nico@yourdomain.onmicrosoft.com Member
# Update the display name
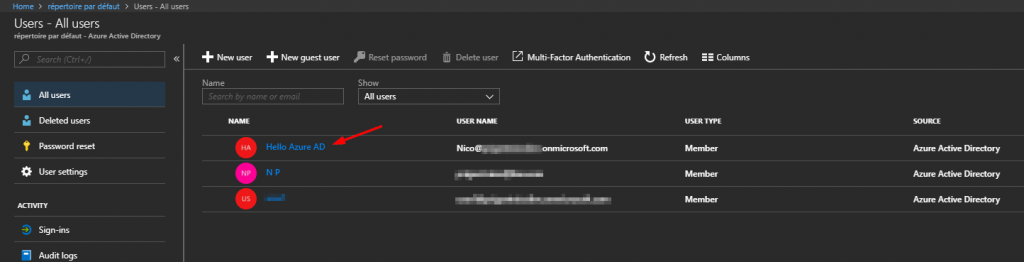
PS C:\WINDOWS\system32> $user.DisplayName = 'Hello Azure AD'
# Check if the value is updated
PS C:\WINDOWS\system32> $user
ObjectId DisplayName UserPrincipalName UserType
-------- ----------- ----------------- --------
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx Hello Azure AD Nico@yourdomain.onmicrosoft.com Member
# Now you can update information in Azure AD
PS C:\WINDOWS\system32> Set-AzureADUser -ObjectId xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx -Displayname $user.Displayname
# Let's confirm if the display name is updated
PS C:\WINDOWS\system32> Get-AzureADUser | ? {$_.ObjectId -eq "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"}
ObjectId DisplayName UserPrincipalName UserType
-------- ----------- ----------------- --------
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx Hello Azure AD Nico@yourdomain.onmicrosoft.com Member
That’s all. Azure AD PowerShell is very useful to manage your Azure AD Users.
Thanks for reading! You can follow me on Twitter @PrigentNico