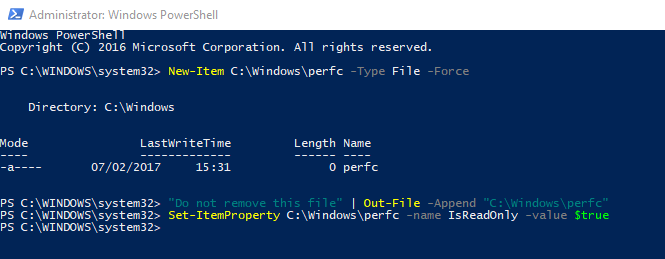
PowerShell can help you to protect against Petya Ransomware by creating the perfc file automatically.
PS > New-Item C:\Windows\perfc -Type File -Force
Directory: C:\Windows
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 07/02/2017 15:31 0 perfc
PS > "Do not remove this file" | Out-File -Append "C:\Windows\perfc"
PS > Set-ItemProperty C:\Windows\perfc -name IsReadOnly -value $true
Output:
Please perform the same steps for perfc.dll and perfc.dat:
PS > New-Item C:\Windows\perfc.dat -Type File -Force
Directory: C:\Windows
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 07/02/2017 15:41 0 perfc.dat
PS > New-Item C:\Windows\perfc.dll -Type File -Force
Directory: C:\Windows
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 07/02/2017 15:42 0 perfc.dll
Check if “perfc” file has been created:
PS > Get-Item C:\Windows\perfc | fl *
Output:
You also can use this full script to patch your computers.
Recommendations
Microsoft recommends to customers that have not yet installed security update MS17-010 to do so as soon as possible. Until you can apply the patch, they also recommend two possible workarounds to reduce the attack surface:
- Disabling SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547
- Adding a rule on your router or firewall to block incoming SMB traffic on port 445
Thanks for reading! You can follow me on Twitter @PrigentNico